GENERAL PURPOSE BPF COUNTER
Our Opensource network monitoring tool pcap_bpfcounter is released!
There must be hundred different network monitoring tools out there, some free, some reasonably priced, some un-reasonably priced. FMADIO has released its opensource "pcap_bpfcounter" utility with an associated FMADIO plugin that works on all our capture systems.
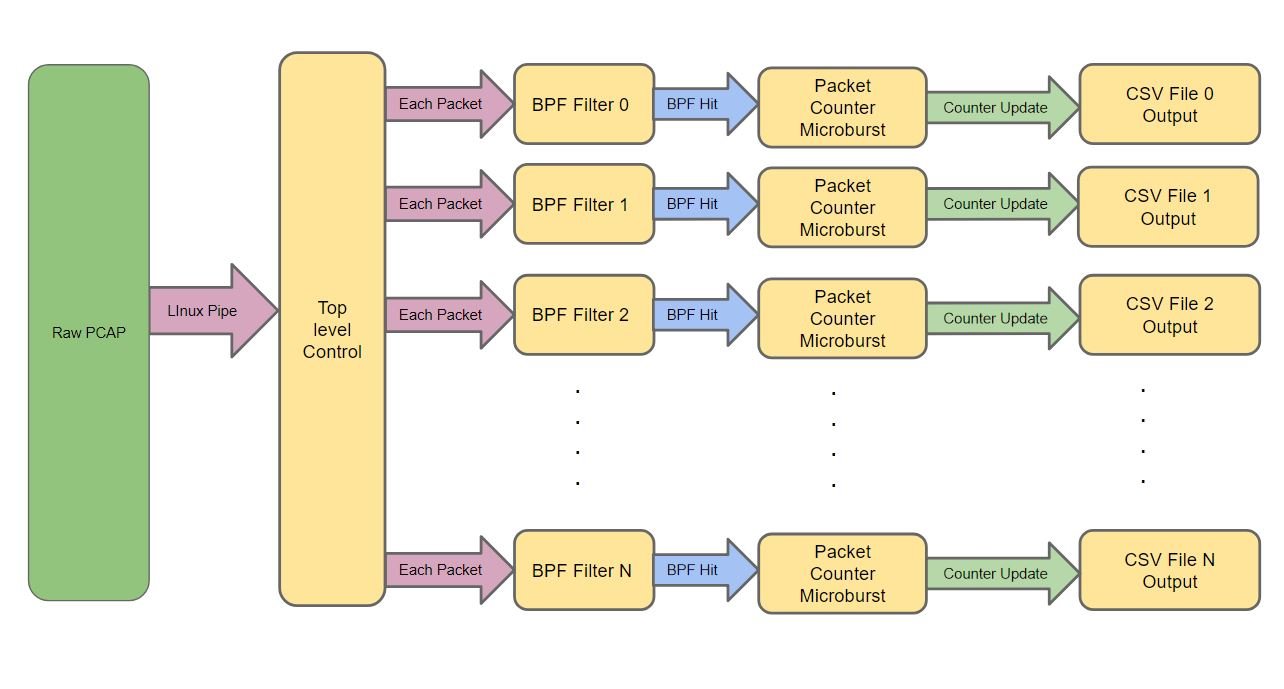
We believe in the UNIX tool philosophy of a small compact utility that does one thing, well. And that one thing is to count packets and calculate bandwidth/microbursts. Sounds simple and it is! but what makes it unique is a user defined near unlimited number of BPF flows to count. It works by sending the same packet though each and every BPF filter defined in the config file. Because the filter is BPF, it enables monitoring of very generic flows (e.g. all tcp/udp), to extremely specific (BPF: vlan 5 and host 192.168.1.90) and anything in between. If you can do it with tcpdump, its literally the same filter engine.
The key point is specifying as many BPF expressions as needed, then running each and every packet though that BPF expression as shown below.
The resulting output is a simple Tab delimited CSV file thats simple for scripts to parse. With one file per BPF filter makes it simple to monitor many different network flows.
BPF Expression: (host 192.168.1.1) Burst Bucket : 100000 nsec Output Time : 60000000000 nsec ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ Time, EpochNS, Packets, Bytes, BurstMax(Mbps), RateMean(Mbps), PctTotal, RMON1_runt, RMON1_64, RMON1_64-127, RMON1_128-255, RMON1_256-511, RMON1_512-1023, RMON1_1024-1518, RMON1_1024-2047, RMON1_2048-4095, RMON1_4096-8191, RMON1_8192 2018-09-06_23:59:23.154.301.928, 1536245963154301928, 1, 250, 20.000, 0.000, 1.000000, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0 2018-09-07_00:00:23.206.032.023, 1536246023206032023, 761, 128760, 101.440, 0.017, 0.456052, 309, 189, 262, 0, 0, 0, 0, 0, 0, 0, 0 2018-09-07_00:01:23.216.361.437, 1536246083216361437, 1524, 261516, 191.040, 0.018, 0.451980, 312, 189, 262, 0, 0, 0, 0, 0, 0, 0, 0 2018-09-07_00:02:23.230.927.657, 1536246143230927657, 2279, 388396, 101.440, 0.017, 0.457989, 306, 191, 258, 0, 0, 0, 0, 0, 0, 0, 0 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Configuration is even simpler, we use a LUA configuration file as shown below. For more complicated networks you could generate this config file.
-- how often to generate output log entries in nano seconds
SetUpdateRate(60e9)
-- create pipelines
CreatePipeline(
{
["Name"] = "everything",
["BPF"] = "", -- no BPF filter
["RE"] = "",
["Output"] = "/mnt/remote0/fmadio000.stats",
["BurstTime"] = 100e3, -- time bucket to calculate microburtst statistics
})
CreatePipeline(
{
["Name"] = "everything-tcp",
["Output"] = "/mnt/remote0/fmadio000.stats",
["BPF"] = "tcp",
["RE"] = "",
})
CreatePipeline(
{
["Name"] = "everything-udp",
["Output"] = "/mnt/remote0/fmadio000.stats",
["BPF"] = "udp",
["RE"] = "",
})
.
.
.
.And last but not least. The best thing is the results can be written out to an NFS server. On FMADIO packet capture systems you can automatically mount NFS shares and write the resulting information to a centralized location.
Check it out on GitHub or contact us for the FMADIO plugin.